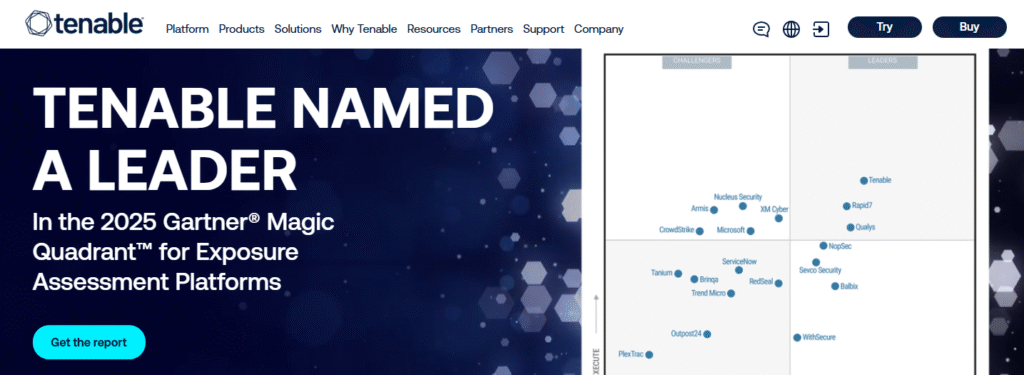
Tenable is a leading provider of cybersecurity solutions that empower organizations to proactively identify, manage, and mitigate vulnerabilities. 🌐
From its powerful Tenable Nessus vulnerability scanner to its comprehensive exposure management platform, Tenable offers robust tools to ensure your organization’s digital infrastructure remains secure. 🚀

Try Tenable Free – Scan Your First Assets 🔍
Whether you’re a small business or a large enterprise, Tenable provides the resources needed to safeguard against cyber threats.
Ready to dive deeper into what Tenable has to offer? Let’s explore!
What is Tenable Nessus?
Tenable Nessus 🛡️ is one of the world’s most trusted vulnerability scanners, designed to help organizations identify security risks in their systems, software, and network configurations.

Nessus performs comprehensive scans 🔍 to detect vulnerabilities like unpatched software, misconfigurations, and potential security holes.
By utilizing Nessus, businesses can quickly pinpoint weaknesses in their infrastructure 🖥️ and take action before attackers can exploit them.
With its robust scanning capabilities, Tenable Nessus ensures that you’re always one step ahead in maintaining a secure environment.
🔑 Key Features of Tenable

Tenable isn’t just a basic scanner it’s a full cyber exposure and risk management platform with a wide range of powerful capabilities designed to protect modern IT environments.
Here are the main features you should include in your article:
1️⃣ Continuous Vulnerability Discovery & Assessment 🔍
Tenable doesn’t scan once and stop it continuously monitors your entire IT environment for new security weaknesses. The moment a new device, software update, or configuration change appears, Tenable checks it for vulnerabilities.
👉 Why this matters:
Cyber threats don’t wait for weekly scans. Continuous discovery ensures no blind spots, especially in fast-changing cloud and hybrid environments.
2️⃣ Risk-Based Vulnerability Management (RBVM) ⚠️
Not all vulnerabilities are equally dangerous and Tenable understands this well. Instead of flooding you with thousands of alerts, Tenable prioritizes vulnerabilities based on real-world risk, exploit availability, and business impact.
👉 Why this matters:
Security teams save time by fixing what can actually be exploited, not just what looks severe on paper.
3️⃣ Asset Discovery & Inventory 🖥️☁️
Tenable automatically finds and tracks all assets across your organization including laptops, servers, cloud workloads, containers, IoT, and OT devices.
👉 Why this matters:
You can’t protect what you don’t know exists. Asset discovery ensures every device and service is visible, reducing hidden attack surfaces.
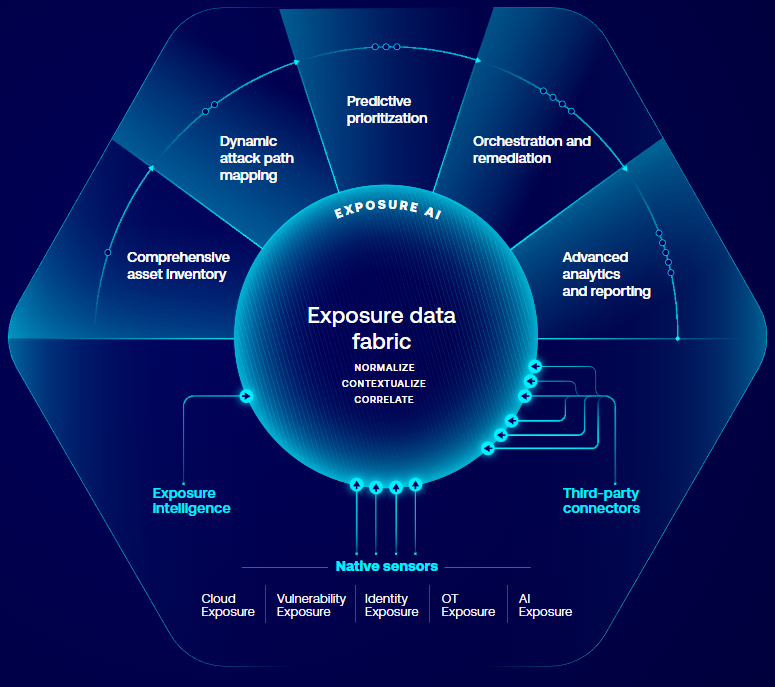
4️⃣ Exposure Management & Cyber Risk Analytics 📊
With Tenable One, the platform goes beyond vulnerabilities and shows total cyber exposure across identities, cloud misconfigurations, web apps, and OT environments all in one dashboard.
👉 Why this matters:
Instead of isolated tools, you get a single source of truth for organizational risk, helping leadership make smarter security decisions.
5️⃣ Predictive Prioritization (VPR™ Scoring) 🧠
Tenable uses machine learning and threat intelligence to calculate Vulnerability Priority Ratings (VPR). These scores predict which vulnerabilities are most likely to be exploited in the real world.
👉 Why this matters:
You fix issues before attackers exploit them, not after damage is done.
6️⃣ Advanced Dashboards & Reporting 📈
Tenable provides customizable dashboards that convert complex vulnerability data into clear visual insights. These dashboards work for both technical teams and executives.
👉 Why this matters:
Security teams get deep technical views, while management gets high-level risk clarity without confusion.
7️⃣ Real-Time Monitoring & Instant Alerts 🚨
Tenable continuously monitors your environment and sends real-time alerts when new vulnerabilities, misconfigurations, or risky assets appear.
👉 Why this matters:
Instead of finding problems days or weeks later, your security team gets notified immediately, reducing response time and damage.
8️⃣ Compliance & Policy Auditing 🧾
Tenable helps organizations meet industry and regulatory standards by checking systems against security benchmarks and compliance frameworks.
👉 Why this matters:
Compliance failures can lead to fines and reputational damage. Tenable highlights exact gaps so audits become easier and faster.
Start Your Free Tenable Trial Today 🚀
9️⃣ Custom Reports, Filters & Saved Views 🗂️
Tenable allows users to create custom dashboards, filters, and saved searches based on teams, assets, severity, or risk level.
👉 Why this matters:
Security teams can focus only on what matters to them instead of digging through thousands of results every time.
🔟 Seamless Integrations & Workflow Automation 🔗
Tenable integrates with SIEM tools, ticketing systems, DevOps pipelines, and other security platforms to automate remediation workflows.
👉 Why this matters:
Vulnerabilities can automatically generate tickets, alerts, or workflows reducing manual effort and speeding up fixes.
1️⃣1️⃣ Cloud Security & Misconfiguration Detection ☁️
Tenable scans cloud environments to detect risky configurations, exposed services, and security gaps across AWS, Azure, and other cloud platforms.
👉 Why this matters:
Cloud misconfigurations are one of the top causes of breaches. Tenable helps prevent these before attackers find them.
1️⃣2️⃣ OT & IoT Security Visibility 🏭📡
Tenable provides visibility into Operational Technology (OT) and IoT devices, including industrial systems that traditional scanners often miss.
👉 Why this matters:
OT and IoT systems are high-value targets but often poorly secured. Tenable helps protect critical infrastructure.
✒️ If you want a deeper, hands-on look at how vulnerability scanning works in real environments, this guide on vulnerability scanning with Tenable Nessus explains the scanning process with practical examples and workflows.
⚙️ How Tenable Works (Step-by-Step Explained Simply)
This section helps users understand the product flow and improves time on page + SEO trust.
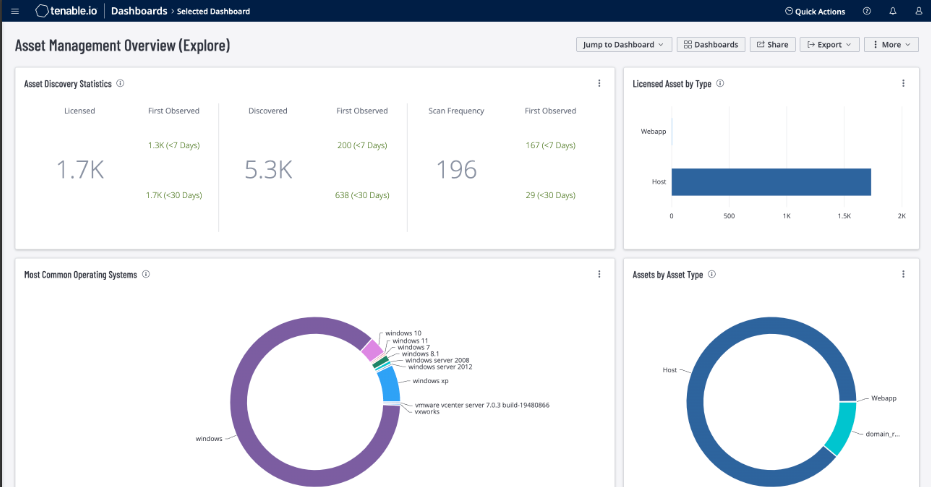
🔹 Step 1: Asset Discovery – “Know What You Have” 🖥️☁️
First, Tenable automatically discovers all assets in your environment. This includes:
- Servers & endpoints
- Cloud workloads
- Network devices
- IoT & OT systems
Tenable scans both on-premise and cloud environments, ensuring nothing stays hidden.
🔹 Step 2: Vulnerability Scanning – “Find the Weak Points” 🔍
Once assets are discovered, Tenable scans them for:
- Known vulnerabilities (CVEs)
- Missing patches
- Misconfigurations
- Weak security settings
It uses one of the world’s largest vulnerability databases, updated continuously.
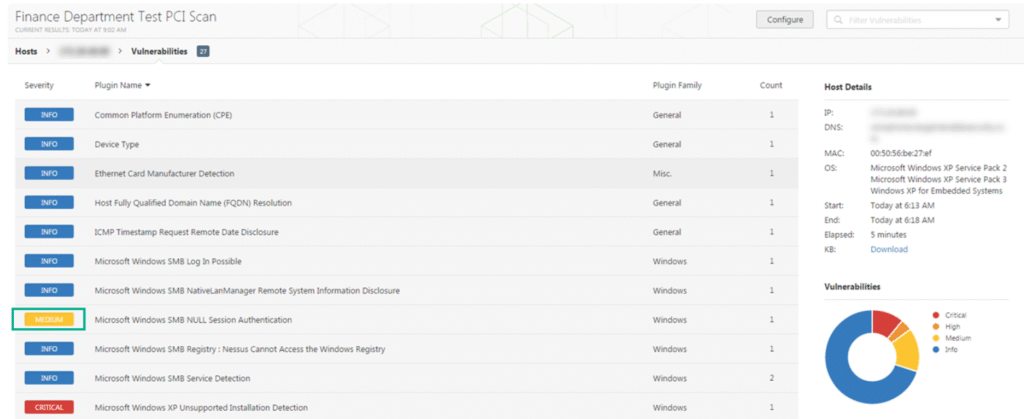
🔹 Step 3: Risk Analysis & Prioritization ⚠️
Instead of dumping thousands of alerts, Tenable analyzes each vulnerability using:
- Threat intelligence
- Exploit availability
- Asset importance
- Business impact
This generates VPR (Vulnerability Priority Rating) and exposure scores.
👉 Why this matters:
Teams know exactly what to fix first, saving time and reducing real risk.
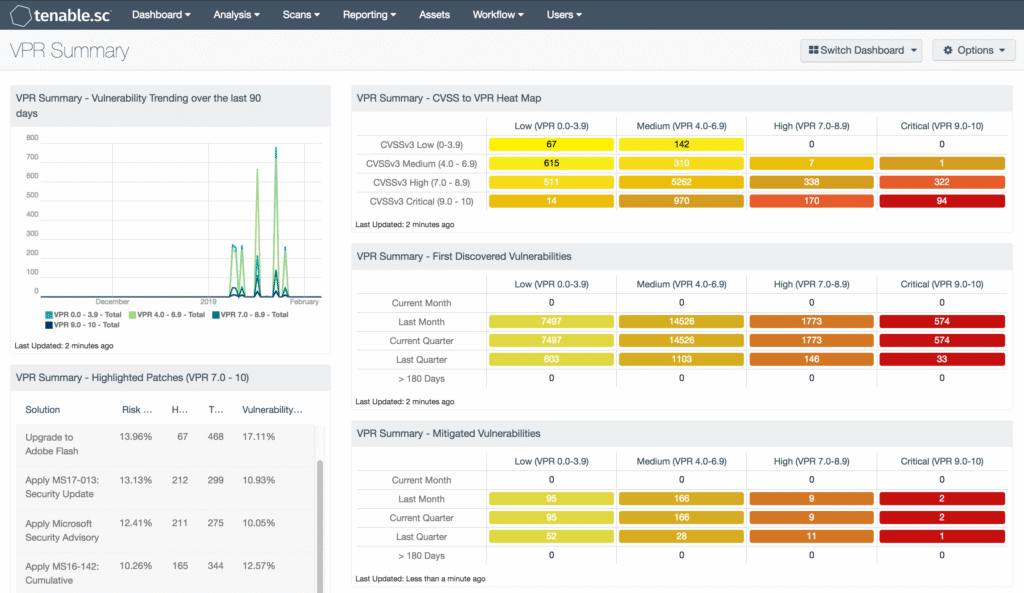
🔹 Step 4: Exposure Management View 📊
Tenable combines vulnerabilities, assets, identities, and cloud risks into a single exposure view (especially with Tenable One).
You can see:
- Overall cyber exposure score
- High-risk areas
- Trending risks over time
👉 Why this matters:
Leadership and security teams get a clear big-picture view, not scattered data.
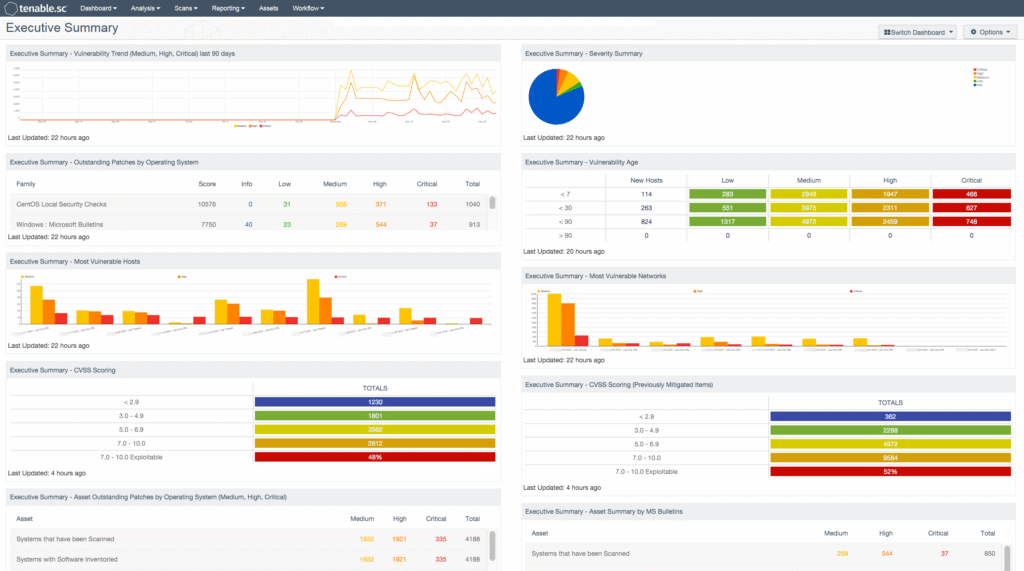
🔹 Step 5: Reporting & Alerts 🚨
Tenable generates:
- Automated reports
- Real-time alerts
- Custom dashboards
Reports can be shared with IT teams, compliance officers, or management.
👉 Why this matters:
Security becomes actionable and communicable, not just technical noise.
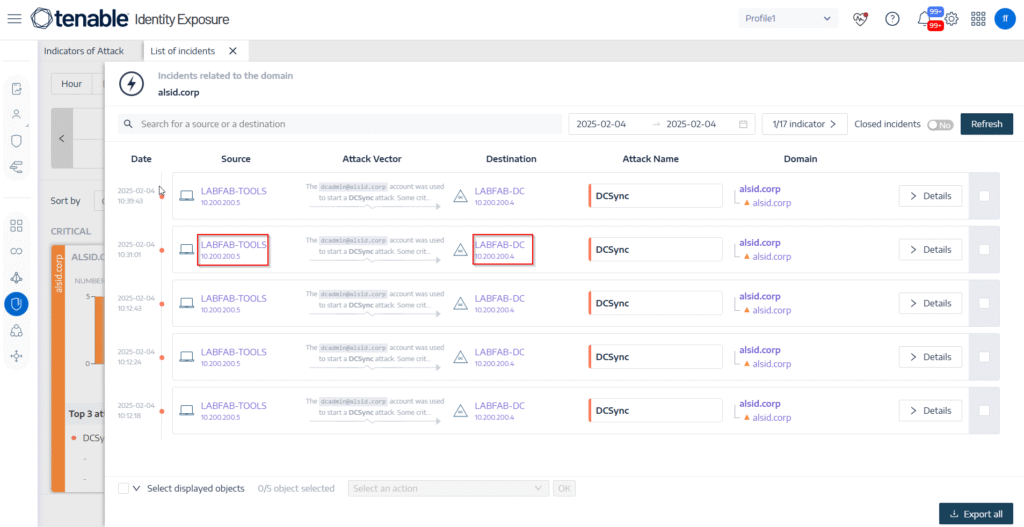
🔹 Step 6: Integration & Remediation 🔗
Finally, Tenable integrates with:
- Ticketing tools
- SIEM platforms
- DevOps workflows
Vulnerabilities can automatically create tickets or trigger workflows for faster fixes.
👉 Why this matters:
This reduces manual work and speeds up real remediation, not just detection.
Get Started with Tenable – Free Trial Available 🆓
🧩 Tenable Products Explained (What Each Tool Does)
Tenable is not a single tool it’s a complete security ecosystem. Below is a clear, simple explanation of its main products, so users immediately understand which one they actually need.
🛡️ 1️⃣ Tenable Nessus (Vulnerability Scanner)
Best for: Vulnerability scanning & assessments
Tenable Nessus is the most popular and widely used product in the Tenable lineup. It focuses on finding vulnerabilities in systems, networks, servers, and applications.

What Nessus does well:
- Scans for thousands of known vulnerabilities (CVEs)
- Detects missing patches & weak configurations
- Easy to deploy and use compared to enterprise tools
👉 Why users love it:
It’s powerful, accurate, and trusted by security professionals worldwide.
🧠 2️⃣ Tenable One (Unified Exposure Management Platform)
Best for: Large organizations & enterprise security teams
Tenable One is Tenable’s all-in-one exposure management platform. It combines multiple security signals into a single dashboard.
What Tenable One includes:
- Vulnerability management
- Identity exposure
- Cloud security risks
- OT & IoT visibility
- Advanced analytics & risk scoring
👉 Why this matters:
Instead of using multiple tools, teams get one unified view of cyber risk.
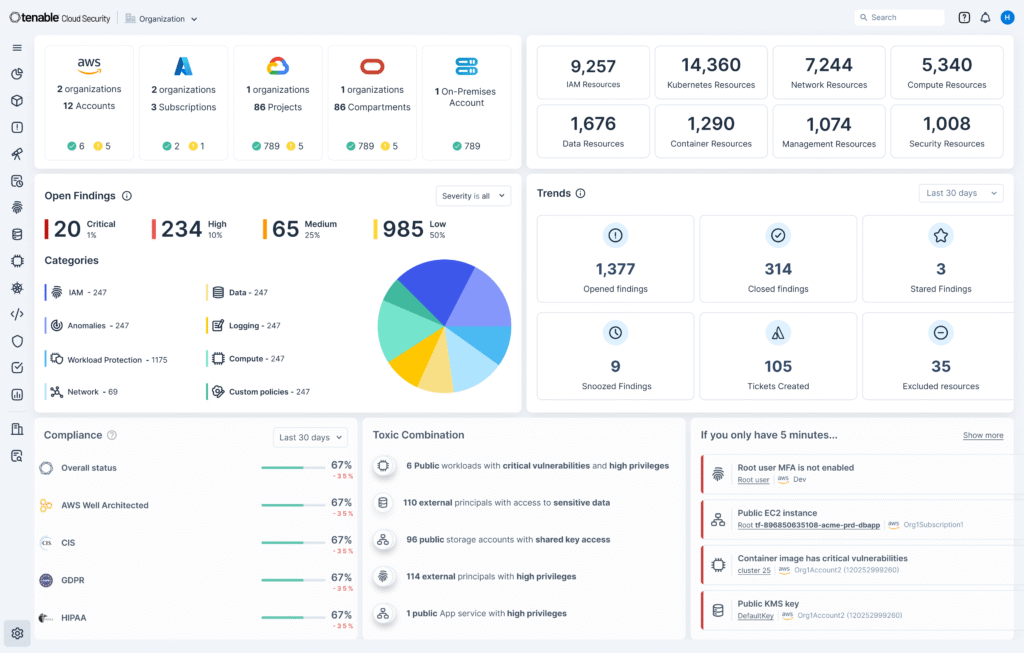
☁️ 3️⃣ Tenable Cloud Security
Best for: Cloud-native & hybrid environments
Tenable Cloud Security focuses on protecting cloud infrastructure like AWS, Azure, and other cloud services.
Key capabilities:
- Detects cloud misconfigurations
- Identifies exposed services & permissions
- Helps reduce cloud-based attack surfaces
👉 Why this matters:
Most modern breaches happen due to cloud misconfigurations, not malware.
🏭 4️⃣ Tenable OT Security
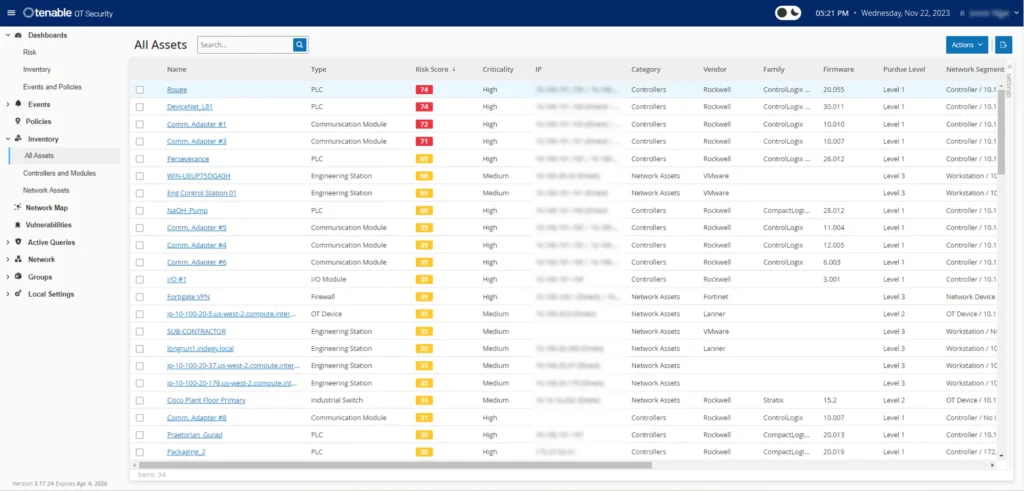
Best for: Industrial, manufacturing & critical infrastructure
Tenable OT Security is designed to protect operational technology (OT) environments like factories, utilities, and industrial networks.
What it secures:
- Industrial control systems
- IoT devices
- Legacy systems not designed for security
👉 Why this matters:
OT systems are critical and often can’t be patched easily visibility is essential.
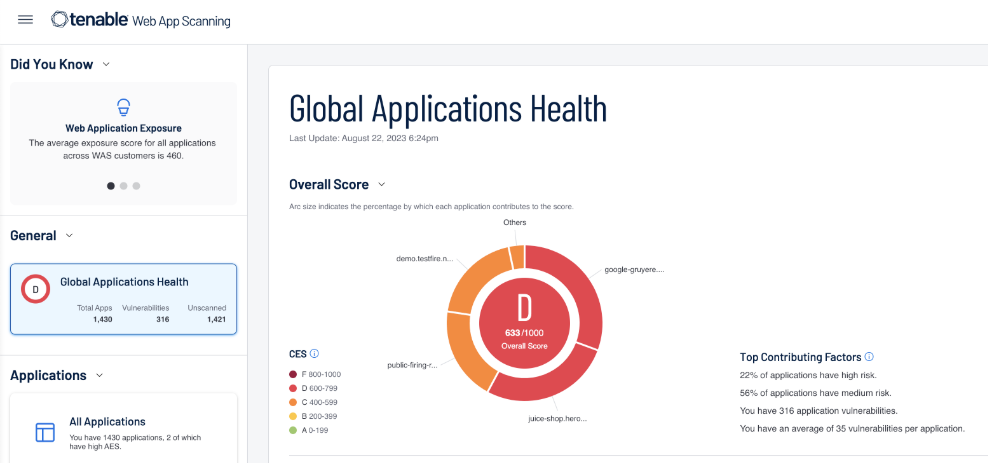
🌐 5️⃣ Tenable Web App Scanning (If Applicable)
Best for: Web applications & online platforms
This tool helps identify vulnerabilities in web applications such as:
- SQL injection
- Cross-site scripting (XSS)
- Application misconfigurations
👉 Why this matters:
Web apps are public-facing and prime attack targets.
Test Tenable Risk Scanning Free Today ⚡
💰 Tenable Pricing
Tenable does not follow simple fixed pricing like basic SaaS tools. Its pricing depends on product type, environment size, and usage, which is common in enterprise cybersecurity software.
🧾 Is Tenable Free or Paid?
✅ Yes, Tenable offers both free and paid options, depending on the product.
- Nessus Essentials → Free version
- Paid Tenable products → Custom pricing
This hybrid model helps beginners start free and enterprises scale securely.
🛡️ Tenable Nessus Pricing (Professional vs Expert)

| Plan | License Type | Price (1 Year) | Best For | Key Features |
|---|---|---|---|---|
| Nessus Professional | 1-Year License | US$431.68 / month US$5,180.20 / year (VAT incl.) | Security professionals, consultants | ✔ Unlimited vulnerability scanning ✔ Real-time vulnerability updates ✔ Pre-built configuration & compliance audits |
| Nessus Expert | 1-Year License | US$628.35 / month US$7,540.20 / year (VAT incl.) | Advanced security teams, external testing | ✔ All Nessus Professional features ➕ Web application scanning ➕ External attack surface discovery scanning |
🔍 Tenable Enterprise & Web Security Pricing

| Product | Billing Model | Price | Best For | Key Features |
|---|---|---|---|---|
| Tenable Vulnerability Management | Per Asset / Year | US$57.82 per asset / year Example: 100 assets = US$5,782 | Growing teams & enterprises | ✔ Continuous vulnerability monitoring ✔ Risk-based prioritization (VPR) ✔ Asset discovery & inventory |
| Tenable Web App Scanning | 1-Year Subscription | US$7,434 / year | Web apps & API security | ✔ Automated DAST scanning ✔ OWASP Top 10 coverage ✔ API & web vulnerability detection ✔ Scans up to 5 FQDNs |
Run Your First Vulnerability Scan Free 🛡️
✅ Tenable Pros & Cons
Pros
- 🔍 Industry-leading vulnerability detection with frequent updates
- ⚠️ Risk-based prioritization (VPR) helps fix the most critical issues first
- ☁️ Excellent asset discovery across on-prem, cloud, IoT & OT
- 📊 Clear dashboards and detailed, customizable reports
- 🏢 Scales well from individual professionals to large enterprises
- 🔗 Flexible deployment (on-prem, cloud, hybrid)
Cons
- 💰 Pricing can be expensive for small teams and startups
- 📚 Advanced features have a learning curve
- ⏳ Most plans are annual no simple monthly billing
- 🌐 Web app scanning is not included in basic Nessus plans
- ✕ Full exposure management requires higher-tier plans
- ✕ Setup for large environments can take time
🎯 Who Should Use Tenable? (And Who Should Avoid It)
✅ Who Should Use Tenable
| User Type | Why Tenable Is a Good Fit |
|---|---|
| Security Professionals & Pentesters | Nessus is one of the most trusted vulnerability scanners with deep, accurate detection 🔍 |
| Mid to Large Enterprises | Tenable scales easily across hundreds or thousands of assets with centralized control 🔒 |
| IT & Security Teams | Risk-based prioritization (VPR) helps teams focus on real threats instead of noise ⚠️ |
| Cloud & Hybrid Organizations | Strong asset discovery and cloud security visibility ☁️ |
| Compliance-Focused Businesses | Built-in policies and reporting help with audits and security standards 📋 |
| Consultants & MSSPs | Nessus Professional/Expert is ideal for scanning multiple client environments 🔮 |
❌ Who Should Avoid Tenable
| User Type | Why Tenable May Not Be Ideal |
|---|---|
| Very Small Teams / Solo Founders | Pricing can feel high if security isn’t a core priority 💰 |
| Non-Technical Users | Advanced dashboards and exposure management have a learning curve 📘 |
| Short-Term or One-Time Users | Annual billing may not suit temporary needs ⏳ |
| Budget-Only Buyers | Cheaper tools exist, but with less accuracy and depth |

🔍 Tenable vs Qualys vs Rapid7
| Feature | Tenable (Nessus) | Qualys | Rapid7 (InsightVM) |
|---|---|---|---|
| Core Focus | Vulnerability & exposure management | Cloud-based security & compliance | Vulnerability + threat detection |
| Vulnerability Accuracy | ⭐⭐⭐⭐⭐ Very high | ⭐⭐⭐⭐ High | ⭐⭐⭐⭐ High |
| Ease of Use | ⭐⭐⭐⭐ Beginner-friendly (Nessus) | ⭐⭐⭐ Steeper learning curve | ⭐⭐⭐ Moderate |
| Risk-Based Prioritization | Yes (VPR scoring) ⚠️ | Yes | Yes |
| Asset Discovery | Excellent (IT, Cloud, IoT, OT) | Strong (mostly cloud-focused) | Good |
| Deployment Options | On-prem, cloud, hybrid | Cloud-only | Cloud-based |
| Pricing Transparency | Moderate | Low (enterprise-heavy) | Moderate |
| Best For | Professionals → Enterprises | Large cloud-first enterprises | Security teams with SOC needs |
Start Your Free Tenable Trial Today 🚀
🛡️ Tenable vs Qualys – Which Is Better?
Tenable wins if:
- You want strong on-prem + hybrid support
- You prefer simpler setup
- You need high accuracy vulnerability scanning
Qualys wins if:
- You are fully cloud-native ☁️
- You want an all-in-one cloud security platform
- Budget is less of a concern
👉 Verdict:
For most users, Tenable is easier to adopt and more flexible than Qualys.
⚡ Tenable vs Rapid7 – Which Should You Choose?
Tenable wins if:
- Your main focus is vulnerability & exposure management
- You want clearer prioritization with VPR
- You don’t need a full SOC platform
Rapid7 wins if:
- You want vulnerability management + SIEM + threat detection
- You already use Rapid7 Insight products
👉 Verdict:
Tenable is stronger for pure vulnerability management, Rapid7 is broader but more complex.
🏁 Final Verdict: Is Tenable Worth It?
Yes — Tenable is absolutely worth it if vulnerability management and cyber risk visibility are critical for your organization.
Tenable stands out because it doesn’t just find vulnerabilities it helps you understand which risks actually matter and what to fix first. With industry-leading accuracy, risk-based prioritization (VPR), and flexible deployment options, Tenable fits both individual professionals and large enterprises.
✅ When Tenable Is the Right Choice
- You need highly accurate vulnerability scanning
- You manage many assets or hybrid/cloud environments
- You want enterprise-grade exposure management
- You prefer a tool trusted globally (Nessus reputation)
❌ When You May Look Elsewhere
- You want the cheapest tool available
- You need a short-term or one-time scan
- You want an all-in-one SOC platform (SIEM + XDR)
⭐ Overall Rating
⭐⭐⭐⭐½ (4.5/5)
Excellent accuracy, strong scalability, and trusted security intelligence with a small learning curve at higher tiers.
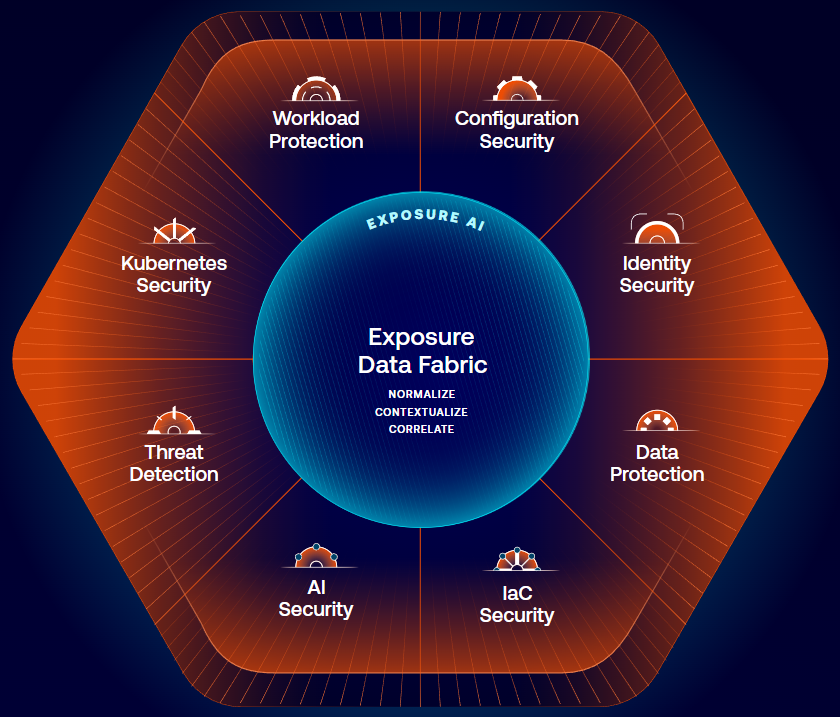
“RELATED ARTICLES”
❓ Frequently Asked Questions (FAQs)
1️⃣ Is Tenable safe and trusted by enterprises? 🔐
Yes, Tenable is widely trusted by enterprises, governments, and security professionals worldwide for accurate vulnerability detection and risk analysis.
2️⃣ Does Tenable work on both Windows and Linux systems? 🖥️
Yes, Tenable supports multiple operating systems, including Windows, Linux, macOS, and various server environments.
3️⃣ Can Tenable be used without installing agents? ⚙️
Yes, Tenable supports both agent-based and agentless scanning, depending on your deployment needs.
4️⃣ How often does Tenable update its vulnerability database? 🔄
Tenable updates its vulnerability plugins frequently, often daily, to ensure detection of the latest security threats.
5️⃣ Is Tenable suitable for beginners in cybersecurity? 🎓
Yes, beginners can start with Nessus Essentials, but advanced Tenable products may require some learning for full use.